IAM Role-Based Access vs AWS Access Key-Based Access
Published on January 9, 2026
In AWS, how you authenticate is just as important as what permissions you grant. Many security incidents happen not because permissions were wrong, but because credentials were managed poorly.
What’s the Right Choice for MyIP Access Integrations?
When memebers onboard onto MyIP Access, one of the most common questions is:
“Should I integrate using IAM Roles or AWS Access Keys?”
This decision directly impacts:
- Security posture
- Blast radius of compromise
- Operational overhead
- AWS best-practice compliance
In this blog, we’ll explain both approaches in the context of MyIP Access, and clearly recommend what you should use in production.
What Is IAM in AWS?
AWS Identity and Access Management (IAM) is the core AWS service that controls:
- Who can access AWS
- What actions they can perform
- Which resources they can access
For MyIP Access, IAM determines how securely we can manage Security Group rules on your behalf.
AWS Access Key-Based Integration (Legacy Approach)
How It Works with MyIP Access
- Customer creates an IAM User
- Generates:
- Access Key ID
- Secret Access Key
- Uploads these keys into MyIP Access
- MyIP Access uses these credentials to:
- Describe Security Groups
- Authorize / revoke IP addresses
Why Some Users Choose This
✅ Easy to understand
✅ Works quickly for testing
✅ Familiar to many beginners
⚠️ Why This Is Risky
❌ Long-lived credentials
❌ High impact if keys leak
❌ Manual rotation required
❌ Violates AWS Well-Architected Security Pillar
❌ Difficult to audit at scale
🚨 If an access key is compromised, attackers can modify your Security Groups instantly
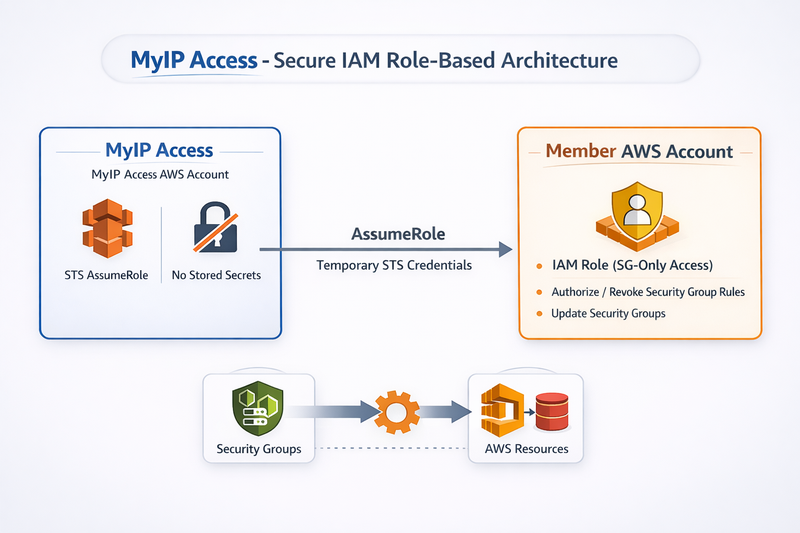
IAM Role-Based Integration (Recommended for MyIP Access)
- Customer creates an IAM Role in their AWS account
- The role:
- Grants only Security Group permissions
- Trusts the MyIP Access AWS Account
- MyIP Access uses STS AssumeRole
- AWS issues temporary credentials
- Credentials automatically expire and rotate
MyIP Access → AssumeRole → Temporary Credentials → Update Security GroupsWhy This Is the Best Choice
✅ No secrets stored
✅ Automatic credential rotation
✅ Least-privilege enforcement
✅ Cross-account secure access
✅ Fully auditable via CloudTrail
✅ Enterprise & compliance friendly
Recommended IAM Policy for MyIP Access
Here’s a minimal, least-privilege policy example:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"ec2:AuthorizeSecurityGroupIngress",
"ec2:RevokeSecurityGroupIngress",
"ec2:DescribeSecurityGroups"
],
"Resource": "*"
}
]
}🔐 MyIP Access never needs full EC2 access — only Security Group operations.
MyIP Access Security Philosophy
At MyIP Access, we follow these principles:
- 🔐 Zero long-lived secrets
- 🔄 Short-lived STS credentials
- 🎯 Least privilege always
- 📜 Full auditability
- 🏢 Enterprise-grade IAM design
That’s why IAM Role-based integration is the default and recommended approach.
Architecture for MyIP Access
Final Recommendation
🏆 IAM Role-based access is the only secure, scalable, and AWS recommanded way to integrate MyIP Access in production.